Free SSL Certificates! | SSL Certificates for Free!
For more than the last decade, I’ve been heavily involved in the process to validate and issue SSL Certificates, the evolution to more robust encryption methods and the general world-shift to using HTTPS as a default for all Web based communications.
The Story so Far
We’ve all been saturated by news stories of hacking, data theft, rigged elections, facebook data mining (with or without permission …) and many, many more, so it’s no surprise that the general trend is to move to communications where our data isn’t transparent to the people that want to control us, be it the good guys or the bad guys.
There is clear internet evolution that has driven these requirement:-
E-commerce
Once businesses & people wanted to buy and sell things online, the need for encrypted communications was an absolution pre-requisites for banks and financial institutions to allow transactions. While they were dragging their feet, services such as PayPal took the opportunity to fill the gap.
Secure Corporate Communications
Businesses required their remote staff to access corporate resources securely with encryption for obvious reasons. Typically provided by PPTP,L2TP/IPSec, SSTP etc.
Secure Email
With the explosion of email as everybody’s go-to communication mechanism, the original ability to read clear content had to go. Microsoft drove a lot of adoption of SSL Certificates through requirements for autodiscover etc. particularly with Exchange Server 2010+ and subsequent versions.
SSL Encryption is simple and it’s all about trust.
To do good business (and plenty of it) you need people to trust you. Before a prospective customer even gets to the stage of trusting you to deliver whatever you are promising there’s the not-so-small matter of proving your identity to make sure there’s a secure platform of trust to build on and Web-browser indicators such as “green bars” or “padlocks” help do this.
Technically, SSL certificates have a “key pair” – public & private which work together to establish a secure, encrypted connection.
To get a certificate, typically you generate a Certificate Signing Request (CSR) from the web host which will serve user connections. This process creates a Private and Public key. The Certification Authority (CA) used this CSR data to create a structure to match the private key without ever seeing this. The CA then issues a certificate that you install on your web server. When a User hits the web server, the whole chain is checked to ensure identity is not compromised.
Of course, anyone can create a certificate themselves (this is often called “Self-Signed”) and many people do this for testing, development and/or Internal-only communications, but only a certificate from a Trusted CA will pass most modern browser checks and allow that green bar or padlock icon to appear. Browsers have a pre-installed list of trusted CA’s (known as Trusted Root CA’s) that they validate against.
The Legacy Arrangement
So what did you do? Simple – you made these decisions and answered these questions:-
- Do I really need a SSL Certificate from a Trusted CA?
- What am I securing? Is this for public consumption or reputation? Can I get away with a Self-Signed if my Users’ are internal?
- Are all CA’s created equally?
- What’s the difference between a certificate from Go Daddy, Verisign, Globalsign etc.? Why the wild variation in cost? Isn’t a cert a cert?
- What validation do I need?
- Standard? EV? High? Etc.
- What’s my budget?
- As above, certificate costs range from £1000’s all the way down to, err, free.
- How many “names” do I need to secure? E.g. Wildcard (*) vs Single Name vs Unified Communications?
- It’s a bit like it’s cheaper to buy a rail weekly ticket if you’re going to make 3 or more journeys.
- If you’re securing a single name project (such as your corporate website on www) then you only need a single cert.
- If you want to secure an Email/Exchange server you can normally buy a single name but get some Subject Alternate Name’s (SAN’s) added for free in what’s called a Unified Communications (UC Cert). This allows you to have a certificate named mail.company.com but also have the normal Exchange names added (autodiscover., owa.).
- If you’re ever going to expand this out (e.g. www, www2, mail, support, autodiscover etc.) to more than three single-names then you should consider a wildcard certificate (e.g. *.company.com) that allows the use of any host name. Make sure every web server will support a wildcard though, particularly legacy web servers and/or appliances.
- How quickly do I need it – do I need self-serve?
- Am I happy to push all certificates requests via a partner, or would I prefer self-service for management purposes if I have a lot of certificates/renewals to manage?
- Do I need to upload CSR’s and download Certificates including some kind of domain validation?
So armed with answers to all of the above, you’d select your service provider and/or CA and pay the corresponding fee.
Having issued many 100’s of certificated from many different authorities, I would make a couple of points:-
- Certain CA’s most definitely have different levels of “reputation” but they are not always consistent. I’ve had clients that have been compromised with most CA’s, although I would hasten to add that the finger of blame doesn’t necessarily lie with the CA as they’re clearly not totally responsible for client security.
- If you’re an end-user then unless your business requires extremely rapid certifcates then self-service probably isn’t a must. If you need this, definitely make sure you can issue yourselves. In the past, where I had many consultants requesting certicates on an almost-daily basis then self-service was an absolute priority.
The Cost
The cost of the certification process can be broken down into:-
- Transaction
- The Actual cost of the certificate (based on 1-3 years timescales), renewable.
- Administration
- The cost of the validation and finance/PO/Procurement process
- Technical
- Implementing the certificate, managing renewals, security, validation.
As an example, I did a quick comparison from TheSSLStore:-
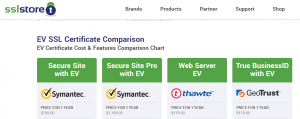
See the difference?!
The Present & Future
So, this has been the scene for many years and we’ve all dropped many hundreds/thousands of £/$ proving we are who we say we are but the landscape has now changed massively with the Let’s Encrypt project which if you haven’t already, go and read up on (https://letsencrypt.org).
Now we have more options – more power to the people!
Let’s Encrypt is backed by lots and lots of organisations, including Mozilla, Google and Facebook. It’s real, it’s secure and it’s not going anywhere.
Let’s Encrypt certificates are managed by you throughout the whole process. You create the CSR. You setup the validation mechanism, including proving domain ownership etc. You receive the certicates. You apply these to your web servers.
Or
You can use some open source tools to automatically deploy and renew which provide wrappers for the Automated Certificate Management Environment (ACME) API that actually performs the operation required for the certificate enrolment process.:-
- For Linux web servers (Apache, NginX etc.),use Certbot (https://certbot.eff.org)
- For Windows web server (IIS), look at tools such as:-
- LetsEncrypt-Win-Simple (https://github.com/Lone-Coder/letsencrypt-win-simple)
- ACMESharp Powershell Commands (https://github.com/ebekker/ACMESharp)
- Certify (http://certify.webprofusion.com/)
Some of the tools, such as Certbot can also handle auto-renewals.
If you need further information, assistance or help setting up Lets Encrypt then please let us know and we’d be happy to help as always!! :-